Recently I've been pretty busy at my new job, so I fell behind a little on my usual open source contributions and project maintenance. I also had the longest streak of no GitHub activity in years this November:
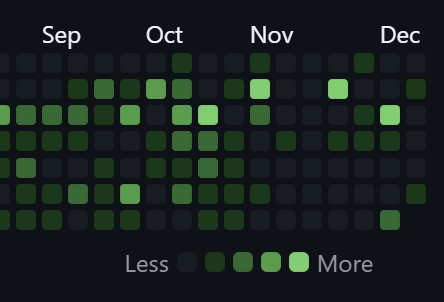
But at the start of December I wanted to get back into the game. I've spent some time cleaning up dependabot updates and more in personal repos and once that was done I thought something is missing...
How did I notice that GitHub's 2FA is broken?
As many of you know, I've been part of the 11ty (eleventy) team for some time now and I've been actively merging stuff to the 11ty community repos during that time, but when I've got to cleaning up my GitHub notifications, I didn't see anything from 11ty. This is weird, because usually there are about 1 to 2 new notifications per day, since 11ty is still fairly popular and people actively want to contribute back and show off what they build with it.
No Notifications
But in place of notifications I just saw this error message:
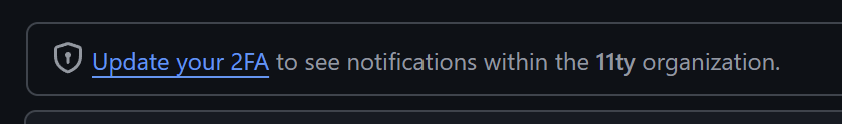
I replaced the part of my phone number that's shown by GitHub with "-" here, to preserve some of my privacy.
My 2FA Setup
Alright then, let's fix that by clicking on the nice link to my 2FA.
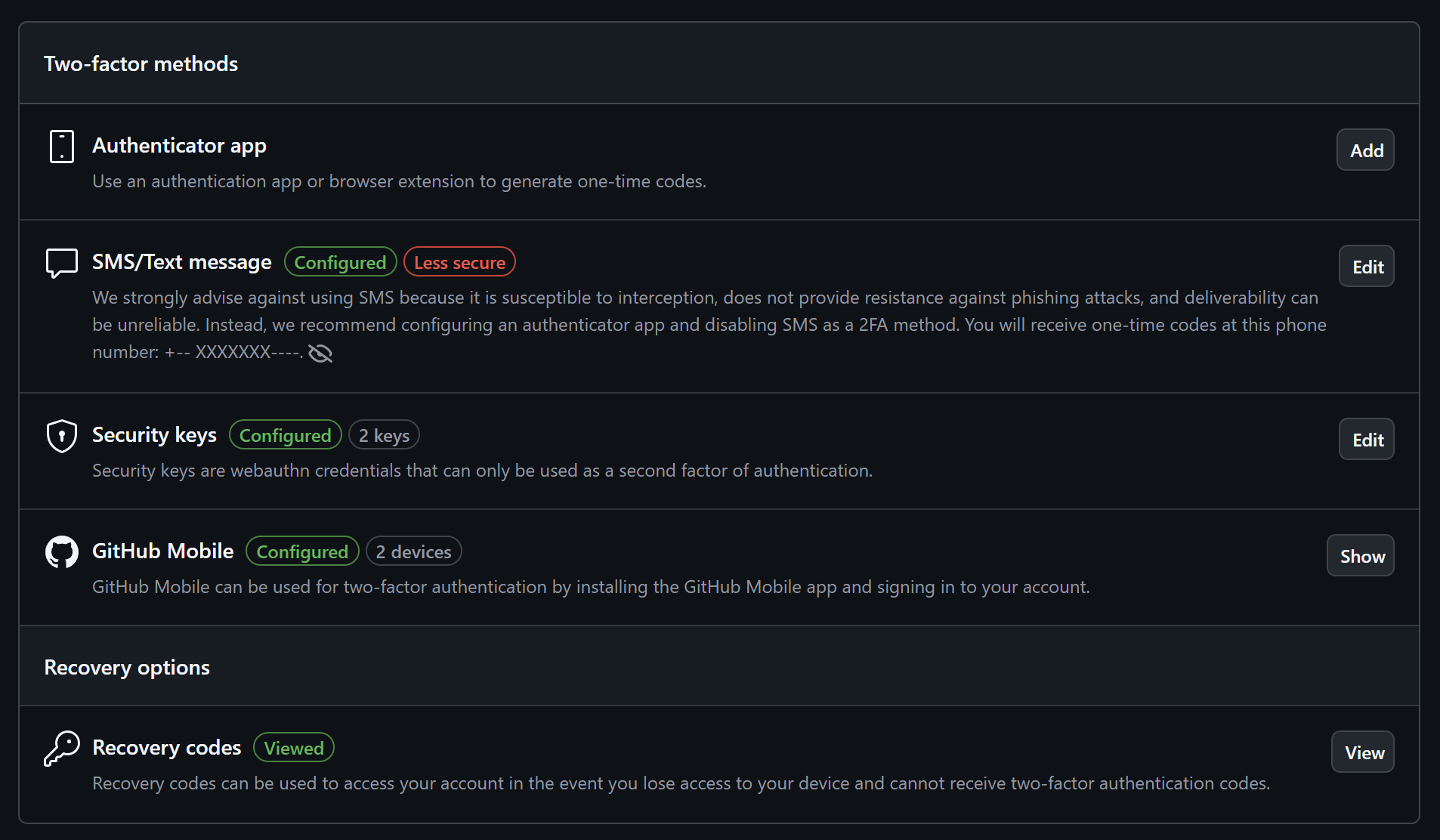
I personally dislike authenticator apps, since they are tied to a device that's quite easy to break and become unrecoverable. I could use one of my security keys as an authenticator app, but that doesn't make sense if I could also directly use the security key as a well... security key.
Great, GitHub shows me that SMS 2FA is less secure, so I probably just need to remove it. That shouldn't be a problem (or so I thought #foreshadowing), since I already have basically every other form of 2FA in place except for an Authenticator App. Also I agree with GitHub's position that you should avoid SMS 2FA wherever you can.
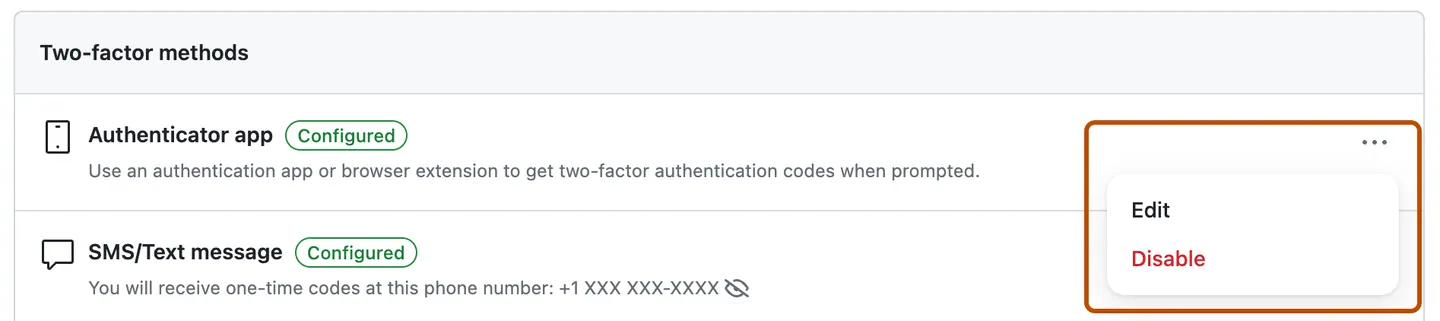
How do I remove SMS 2FA?
That's the question now. The entry has no delete button and also if you click on "edit", there's no option to delete it:
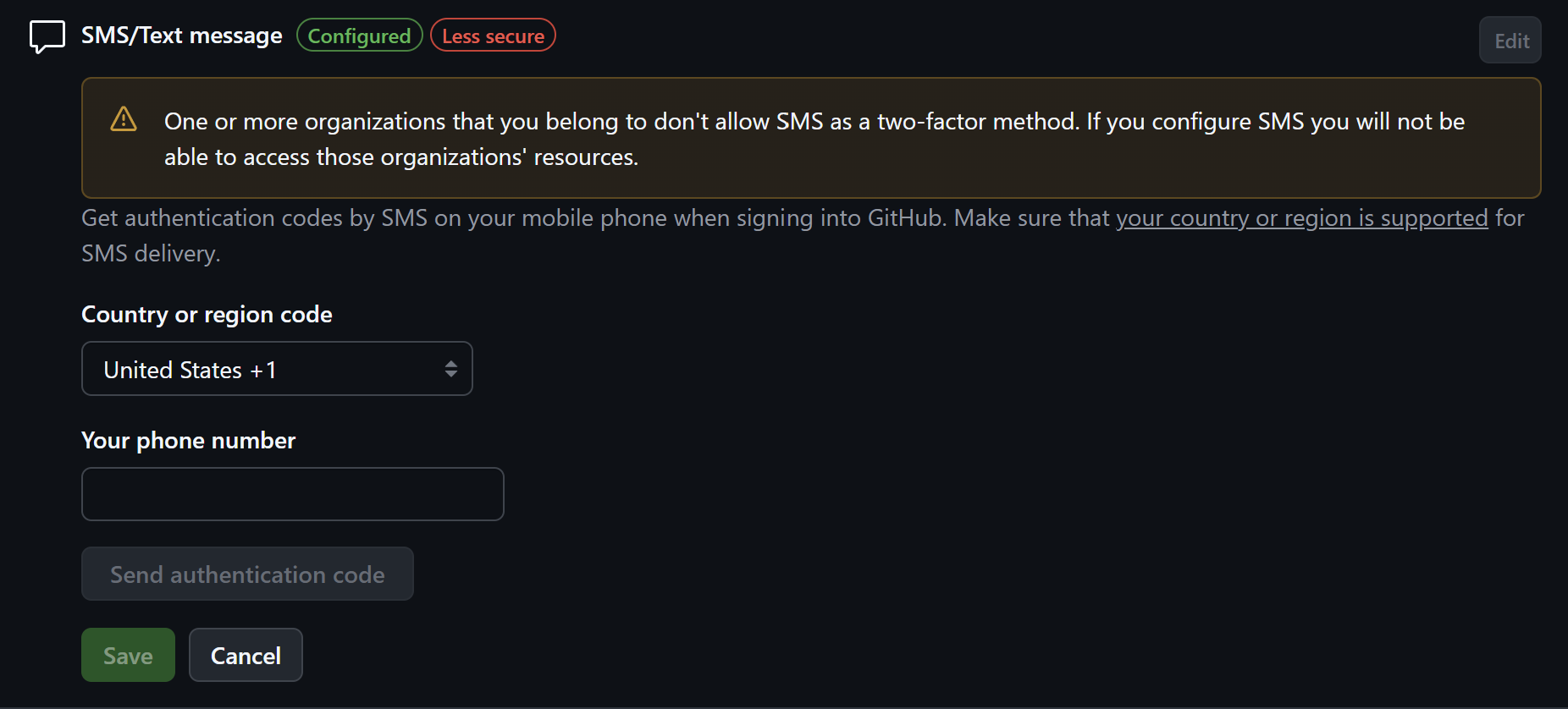
So what would you do at this point?
RTFM
RTFM (or "Read the freaking manual") refers to the action of looking up what you should've been doing instead of stumbling in the dark for hours.
For clear differentiation I'm using the dark theme for my own screenshots and the light theme for GitHub's provided screenshot. That way you can easily tell where they are coming from.
We're a good user, so let's take a look at GitHub's 2FA documentation. Just for reference, let's put the relevant screenshot here:
Did you notice the important difference?
I have no option to disable SMS 2FA as it's shown in the docs!
How to fix this...
Option 1 - Workarounds
This problem is already widely known to the point that there have been discussions in the GitHub Community project sometimes going on for years.
The solution:
- Add an authenticator app as 2FA
- Remove SMS 2FA via the newly appearing option
- Be locked into the authenticator app
This is absolutely annoying, because there's a reason why I didn't add an authenticator app in the first place and also I'd understand that you can't remove all your 2FA options, but I have multiple other options configured and still can't remove SMS - an option GitHub itself claims to be less secure.
Option 2 - GitHub, FIX IT!
Please GitHub, let me remove SMS 2FA when I already have multiple other 2FA methods in place, some of which are right now treated as the gold standard of 2FA. The community has been asking for this for quite some time so this isn't new for you.
What will I do?
I actively support the decision to make secure 2FA a requirement for contributions to 11ty, so I don't think the 11ty project should change anything here.
Probably do the workaround for now, but it will still annoy me and is one of the things driving developers away from GitHub and to other options like Codeberg or GitLab.
I'm still looking forward to contributing again to 11ty, but right now GitHub is making it hard to do so.